Posted by Virus Bulletin on Aug 19, 2014
Andrei Husanu and Alexandru Trifan look at what TCP packet sizes can teach us.
In the weeks running up to VB2014 (the 24th Virus Bulletin International Conference), we will look at some of the research that will be presented at the event. Today, we look at the paper 'Labelling spam through the analysis of protocol patterns', from Bitdefender researchers Andrei Husanu and Alexandru Trifan.
One of the many techniques that have been applied to fight spam is to look at properties of the TCP/IP network traffic and use that to determine the source of the email. If, for instance, the 'fingerprints' of the TCP/IP traffic suggest the email was sent from a Windows XP machine, it is very unlikely to be a legitimate sender. This allows spam filters to drop the connection without inspecting the content of the email or even determining whether the connecting IP address is blacklisted.
In their paper, Andrei and Alexandru take a different look at the network traffic from email senders. They study the way the SMTP data is split into TCP/IP segments and try to see if there are patterns that suggest the sender is a spammer.
TCP traffic is split among multiple IP packets, and the size of these packets is usually determined by the maximum segment size that can be sent between the two ends of the network connection. However, in some cases the way SMTP data is split also says something interesting about the sender of the email.
Typical of some spammers is that they send each recipient the same payload but with a different From: header prepended to it. This From: header is then sent as a separate packet, with a small (and usually variable) size. Another example is email sent from devices using a mobile connection (which, if a direct connection is made to the recipient's mail server, is rarely legitimate). Here, a typical pattern is for the packet sizes to fluctuate.
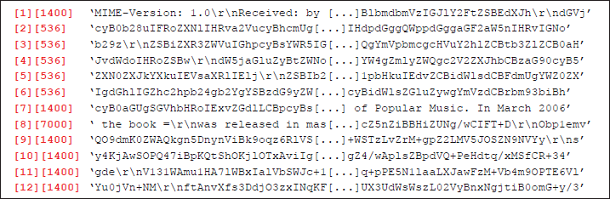
Good spam research has become relatively rare in the past half decade, and I was thus rather pleased to read Andrei's and Alexandru's paper.
Whether this research will be applicable in spam filters, and whether it will result in an improvement to existing technologies is not for me to say, but I do think that this technology might have applications outside of anti-spam technology too. After all, reliably being able to distinguish humans from computers is something that will help in many areas of cybersecurity.
You can now register for VB2014. And if you have some research that you want to share with the security community, why not submit an abstract to fill one of the seven remaining 'last-minute' presentation slots?
Posted on 19 August 2014 by Martijn Grooten