Posted by Virus Bulletin on Aug 21, 2014
Raul Alvarez studies the Neshta prepending file infector.
File infectors can be categorized by how they attach themselves to the host file. A cavity virus attaches itself to the available spaces in the host file; an appending virus attaches its code at the end of a file; and a prepending virus does so at the beginning of the file.
Prepending viruses are usually easy to remove, as the malicious code can simply be cut off to get the restored host file. However, this isn't always the case.
Today, we publish a paper by Raul Alvarez, a researcher for Fortinet, in which he studies the 'Neshta' file infector. Unlike other prepending viruses, Neshta uses a number of tricks that mean the host file can't be restored simply by cutting off the infected part.
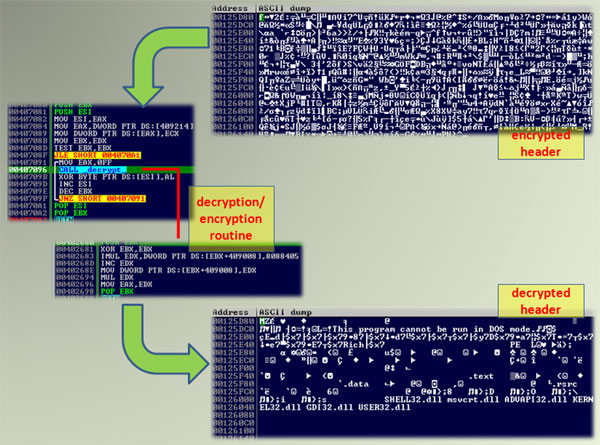
In the paper, Raul explains in detail how Neshta attaches itself to an executable, as well as the encryption it uses to make detection and restoration harder. Hence, while the malware attempts to deter researchers, this paper will help those researchers tasked with cleaning up an infection.
You can download the paper here in HTML format, or here as a PDF (no registration required).
If you like this analysis of an old-fashioned file infector, make sure you also read the paper Raul wrote last month, in which he studied the W32/Daum file infector.
Posted on 21 August 2014 by Martijn Grooten