Posted by Virus Bulletin on Jul 14, 2014
Raul Alvarez studies the unique EPO methodology used by the W32/Daum file infector.
A few months ago, we published an article by Fortinet's Raul Alvarez on the Expiro file infector, which uses an EPO (entry-point obscuring) technique in an attempt to avoid heuristic detection.
In EPO, a file infector doesn't simply change the entry point of the infected executable - which is something that would be easy to detect. Rather, the malware 'patches', as it were, the executable to add a malicious component.
Today, we publish another paper by Raul Alvarez in which he looks at the W32/Daum file infector. Daum, which some AV vendors refer to as Lafee, is an old and relatively simple file infector. However, its unique EPO technique, in which all API calls are changed, makes it worth studying.
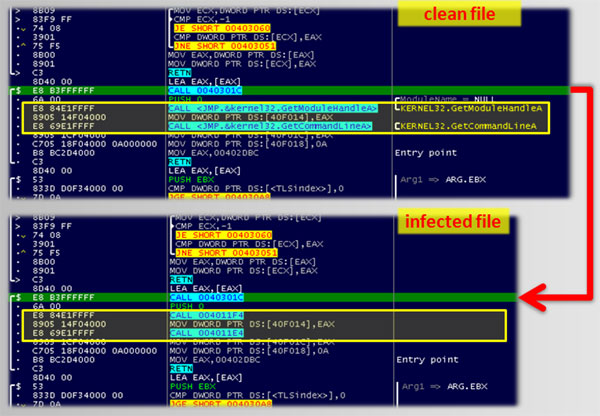
Remember that, as of this month, all papers published through Virus Bulletin are available free of charge. You can download this paper here in HTML format, or here as a PDF (no registration required).
Posted on 14 July 2014 by Martijn Grooten