Posted by Virus Bulletin on Jan 30, 2014
Sysadmins can check hashes of processes against file-checking service database.
Microsoft and Google are known for their fierce competition, but when it comes to security, the tech giants are eager to put that aside. Hence as of this week, Google's VirusTotal has been integrated into Microsoft's Process Explorer.
The planned integration was announced by Sysinternals founder and developer Mark Russinovich (who has written for Virus Bulletin in the past and whose fictional works have also been reviewed in the magazine) on Twitter last October:
Coming soon: Sysinternals tools integration with VirusTotal, starting with Sigcheck— Mark Russinovich (@markrussinovich) October 17, 2013
With yesterday's release of Process Explorer 16.0, the integration was completed.
Process Explorer is a task manager and process monitor that is part of the Windows Sysinternals suite. It gives Windows administrators information on the processes that are running and the resources used by them. It can be very helpful when trying to solve system issues.
While investigating, an administrator may wonder whether a process that is running is actually benign. As of this week, they can choose to send the hash of a process to VirusTotal and the interface will show whether the file has been scanned before and, if it has, how many of several dozen anti-virus products detect it as malicious.
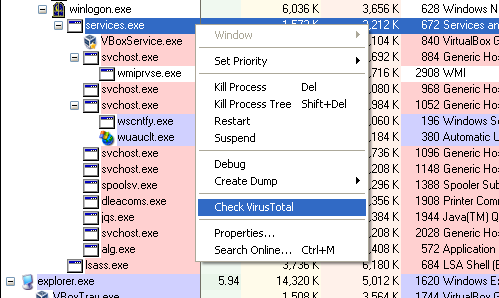
VirusTotal is regularly used by people who then go on to make claims about the performance of anti-virus solutions - something those running the service have long said is a bad idea. However, to find out if a certain file or process is deemed to be malicious by at least some anti-virus products, which in many cases is sufficient information, it is a very useful tool.
In case the file isn't known to VirusTotal - for instance because it is some highly polymorphic or very targeted malware, or because it is an unknown but legitimate program - Process Explorer also lets the user upload the file itself, in order for it to be scanned by a large number of anti-virus products. All in all, I expect that for many system administrators, this integration will be very helpful to confirm whether or not a suspicious process is known to be malicious.
Update: An earlier version of this blog post suggested that only hashes of files were supported. This has now been corrected. Thanks to VirusTotal's Bernardo Quintero for pointing this out.
Posted on 30 January 2014 by Martijn Grooten