Posted by Virus Bulletin on Sep 11, 2013
Too few currently possess the skills to verify standards.
Recent revelations of the NSA's crypto-breaking capabilities have led to calls for better cryptography. But we need more cryptographers too.
In the 2010 edition of their classic book Cryptography Engineering, Bruce Schneier, Niels Ferguson and Tadayoshi Kohno wrote on the SHA family of hash functions:
"At least they have been standardized by NIST, and they were developed by the NSA."
And, in case that would worry some readers, they added a footnote:
"Whatever you may think about the NSA, so far the cryptography it has published has been quite decent."
Given revelations on how the NSA effectively wrote a NIST standard in which it inserted a (mathematical) backdoor, I doubt these sentences will make it to the next edition unaltered.
What the NSA did was undoubtedly bad and will further damage the agency's reputation within the security community. But I think it also says something important about today's cryptography.
Earlier this year I blogged about how Microsoft appears to make HTTP requests to URLs shared via Skype, proving the company had access to the unencrypted content of Skype conversations.
The source code of Skype is closed. Which means that, even before this discovery, if it would matter to you if Microsoft read your conversations (or shared them with third parties) you had no way of verifying that this didn't happen - so it came down to how much you trusted Microsoft.
Now compare that with cryptography standards, which tend to be public. "Dual_EC_DRBG" had been published by NIST for more than a year before two Microsoft researchers, including the aforementioned Niels Ferguson, found a vulnerability that could act as a backdoor.
It is certainly possible that other cryptography standards contain backdoors, inserted by the NSA or other agencies. In an op-ed for Wired, Bruce Schneier writes:
"Certainly the fact that the NSA is pushing elliptic-curve cryptography is some indication that it can break them more easily."
Although he reckons that using longer keys is an easy fix.
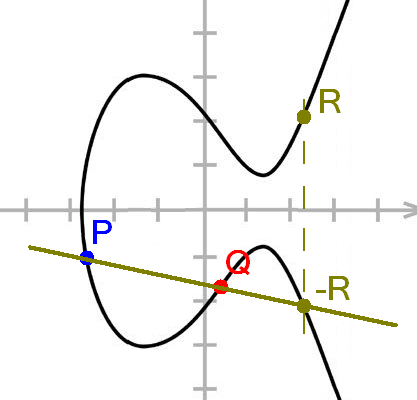
Elliptic curve cryptography (ECC) is generally seen as the next step for cryptography, replacing decades-old algorithms like Diffie-Helman and RSA. It is certainly a powerful tool that will help fend encryption against ever-faster cracking methods. But it has an important weakness: it is very hard to understand.
It is part of a much broader branch of mathematics called arithmetic geometry. This requires a lot of prior knowledge so that, despite its important applications, the vast majority of maths students will never encounter anything of it during their studies. Most of those that do will only briefly touch upon it.
Even those mathematicians that will learn enough about elliptic curves over finite fields to understand ECC and its many pitfalls do not necessarily have a good enough understanding of computer architecture to be able to implement the algorithms or write standards.
All in all, the number of proper experts in ECC is really small. A few thousand, perhaps even fewer. Given how difficult it is to find bugs in other people's code - especially if you're not sure there is a bug in the first place - it could be that there are mathematical backdoors in some of the other standards. Standards that are out there for billions of Internet readers to download and check.
It is also possible that there aren't any more of these backdoors and that most of the standards, including ones that the NSA worked on, are actually quite good. Yet that lack of certainty could cause us to throw away the baby with the bath water.
The ongoing revelations have resulted in an increased interest in cryptography. Hopefully, it will also result in more cryptographers. We need them now more than ever.
Posted on 11 September 2013 by Martijn Grooten