Posted by Virus Bulletin on Jan 29, 2013
Previous victims contacted again and tricked into 'renewing' service.
Phone support scammers have found a new way to make easy money: by calling back people whom they have previously tricked into paying for their services, and tricking the same innocent users into paying for a 'renewal' of the service.
As someone who regularly works from home, I have had my fair share of calls from 'support scammers'. Most readers will be familiar with their tactics: they phone people and tell them they know that their computer has an issue, then use some social engineering to convince their victims that the problem is real, collect payment for their services, then 'fix' the 'problems'.
Like many security researchers who find themselves speaking to such scammers, I tend to play the clueless victim to find out how the scam works. One year ago this week, I managed to make it appear as if I had paid and thus got an interesting insight into what is done to 'fix' the PC. As it turns out, the scammers run a number of free security tools, some of which will actually improve the state of the machine.
Yesterday, I received yet another such call which, to my surprise, referred to the conversation I had a year ago. Then I had paid for one year's protection and this was up for renewal. Unlike previous experiences, when the spammers took their time to convince me I had a problem with my PC, this time they got straight to the point: I had to give the caller remote access (via AMMYY) to my PC, upon which they downloaded Advanced WindowsCare, a legitimate, if somewhat dubious product that has been used by scammers before. It reported that my PC had thousands of errors and thus it was important for me to pay to be protected for another year.
I did not question the fact that my PC was badly infected, even though I was supposed have paid for protection a year ago. Nor did I ask why the name of the company they called from had changed from PC Optimizers to PC Wizards. But then, they didn't ask me why the machine they were fixing wasn't hiding the fact that it was running inside VirtualBox either.
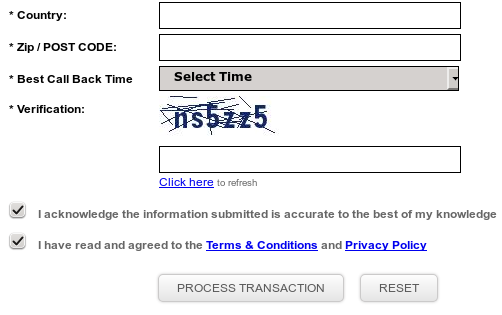
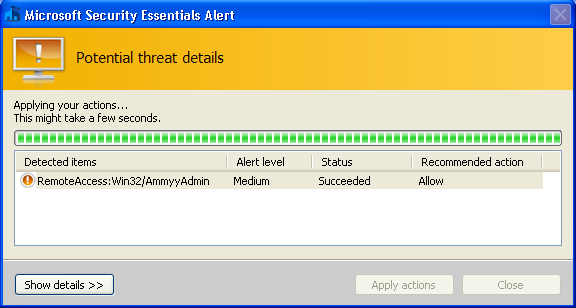
Once again, I bypassed the payment of GBP119 (up from GBP89 last year). Interestingly, 'security' had been added to the payment page by the inclusion of a CAPTCHA. And once again, after the call had ended, the scammers spent some time 'fixing' my PC using a number of free products, such as a disk defragmentation tool. To finish off, they installed the free anti-virus product Microsoft Security Essentials and used it to run a thorough scan of the machine. It reported one potential threat: the AMMYY remote access tool the scammers had installed themselves.
While it is easy to laugh at the scammers' lack of professionalism, they have taken advantage of many victims in the past: people who have become worried after hearing the many stories about malware infections, or people for whom the call just 'made sense'. I have spoken to someone who received a call, supposedly from Microsoft, shortly after having contacted the company himself about a problem with his PC; hence he never questioned the veracity of the callers' claims.
I have also seen people who seemed genuinely happy with the service provided (in one case someone even wrote a poem on the scammers' Facebook page), and it's good to keep in mind that tools like disk defragmentation do tend to improve performance. It is thus not surprising that many previous victims will fall for the same scam again - which means there is still a lot of work for us to do: to catch the scammers and educate the users.
Posted on 29 January 2013 by Martijn Grooten